TL;DR, The Reserve Bank of India (RBI) is steering a shift from traditional OTP-based authentication in response to the rising incidents of online fraud, including over 95,000 cases of UPI fraud reported in the fiscal year 2022-23. This article explores vulnerabilities inherent in OTP systems, such as susceptibility to social engineering and phishing attacks, and discusses the potential of Verifiable Credentials as an alternative to OTPs.
In a groundbreaking move that could redefine the landscape of digital payment security, the Reserve Bank of India (RBI) has recently signaled its intention to move away from the conventional one-time password (OTP) based authentication system. This shift is in response to the increasing online fraud cases, with India reporting over 95,000 cases of UPI fraud in the fiscal year 2022-23.
RBI Governor Shaktikanta Das, during a monetary policy statement address, said, "With innovations in technology, alternative authentication mechanisms have emerged in recent years. To facilitate the use of such mechanisms for digital security, it is proposed to adopt a principle-based “Framework for authentication of digital payment transactions”. Instructions in this regard will be issued separately."
This article explores how Verifiable Credentials (VCs), powered by Hypersign, could be the key to a more secure, efficient, and user-centric digital payment ecosystem.
What is the problem with OTPs?
One of the fundamental vulnerabilities of OTP systems is their susceptibility to social engineering and phishing attacks. An attacker can deceive a user into sharing their OTP, allowing unauthorized access to the user's account or enabling fraudulent transactions.
Verifiable Credentials (VCs) address this issue by fundamentally altering the authentication mechanism. Unlike OTPs, which can be intercepted or deceitfully obtained from the user, VCs rely on cryptographic proof of identity that is securely stored in the user's digital wallet and cannot be shared unintentionally. The authentication process with VCs involves a challenge-response mechanism where the user's identity and transaction authorization are cryptographically verified without transmitting sensitive information that an attacker could exploit. This method ensures that even if an attacker could somehow prompt a user for a VC, they would not be able to replicate the cryptographic proof required for transaction authentication, thus significantly mitigating the risk of fraud.
OTPs VS Verifiable Credentials (VCs)
OTPs and VCs differ in their operational frameworks and security methodologies. OTPs are transient codes sent to users via SMS, email, or an authentication app, valid for a single transaction or login session. Their security is based on the assumption that only the legitimate user has access to the received code. However, OTPs can be intercepted or obtained through social engineering, making them vulnerable to unauthorized access.
On the other hand, VCs are based on cryptographic principles, utilizing digital signatures and blockchain technology to ensure the integrity and authenticity of the credentials. They do not rely on a single point of failure (such as a code that can be intercepted) and provide a more robust security framework by enabling the user to prove their identity and permissions without exposing sensitive information. This cryptographic approach offers a higher degree of protection against phishing, man-in-the-middle attacks, and other forms of digital fraud that plague OTP systems.
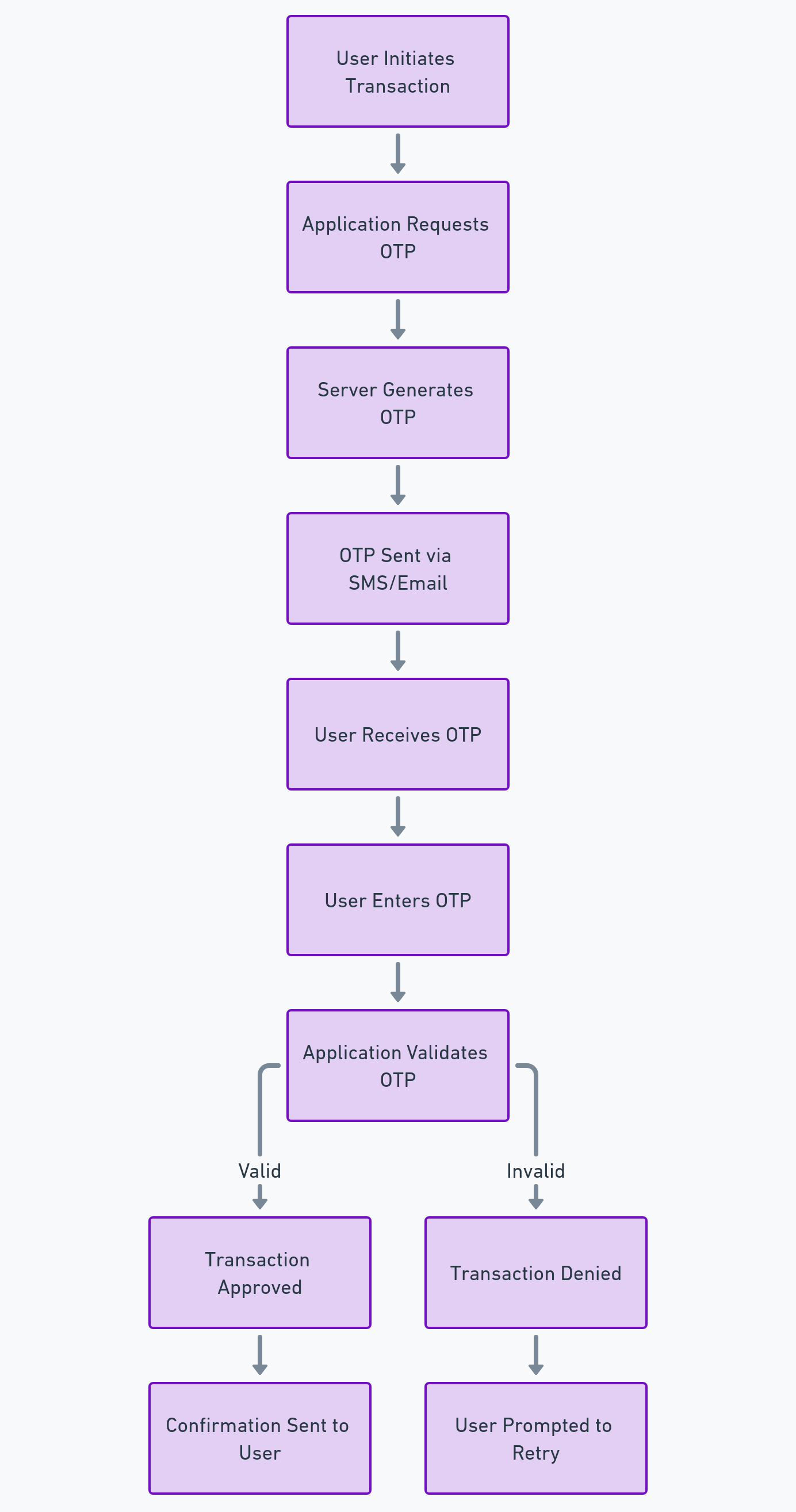
Let’s understand how the OTP system works with the help of a diagram:
Overview of Verifiable Credentials (VCs)
At its core, a Verifiable Credential is a digital document that is cryptographically signed by an issuer, such as a bank or financial institution. This document asserts certain claims about an individual, for instance, their identity, account ownership, or transaction authorization. Unlike traditional credentials, which rely on centralized verification systems, VCs use decentralized identifiers (DIDs) and blockchain technology to enable a trustless verification process.
Decentralized Identifiers (DIDs)
DIDs are a foundational element of the VC ecosystem. They are unique, persistent identifiers that enable a VC to be verifiably linked to the entity it represents without relying on any central authority. DIDs are stored on a blockchain, providing immutability and transparency, which ensures that any attempt to tamper with the credential can be easily detected and prevented.
Cryptographic Signatures
VCs are protected by cryptographic signatures, which serve two primary functions:
- Authentication: The signature verifies that the credential comes from a trusted issuer and that it has not been altered since it was issued.
- Non-Repudiation: It prevents the issuer from denying the issuance of the credential and the holder from denying the presentation of the credential.
Zero-Knowledge Proofs (ZKPs)
ZKPs are a cryptographic method that allows one party (the prover) to prove to another party (the verifier) that a statement is true, without revealing any information beyond the validity of the statement itself. In the context of VCs, ZKPs can be used to prove that a user possesses a valid credential or meets certain criteria without disclosing the credential's contents. This is particularly useful for financial transactions, where privacy and data minimization are crucial.
Integrating VCs into Digital Payment Systems
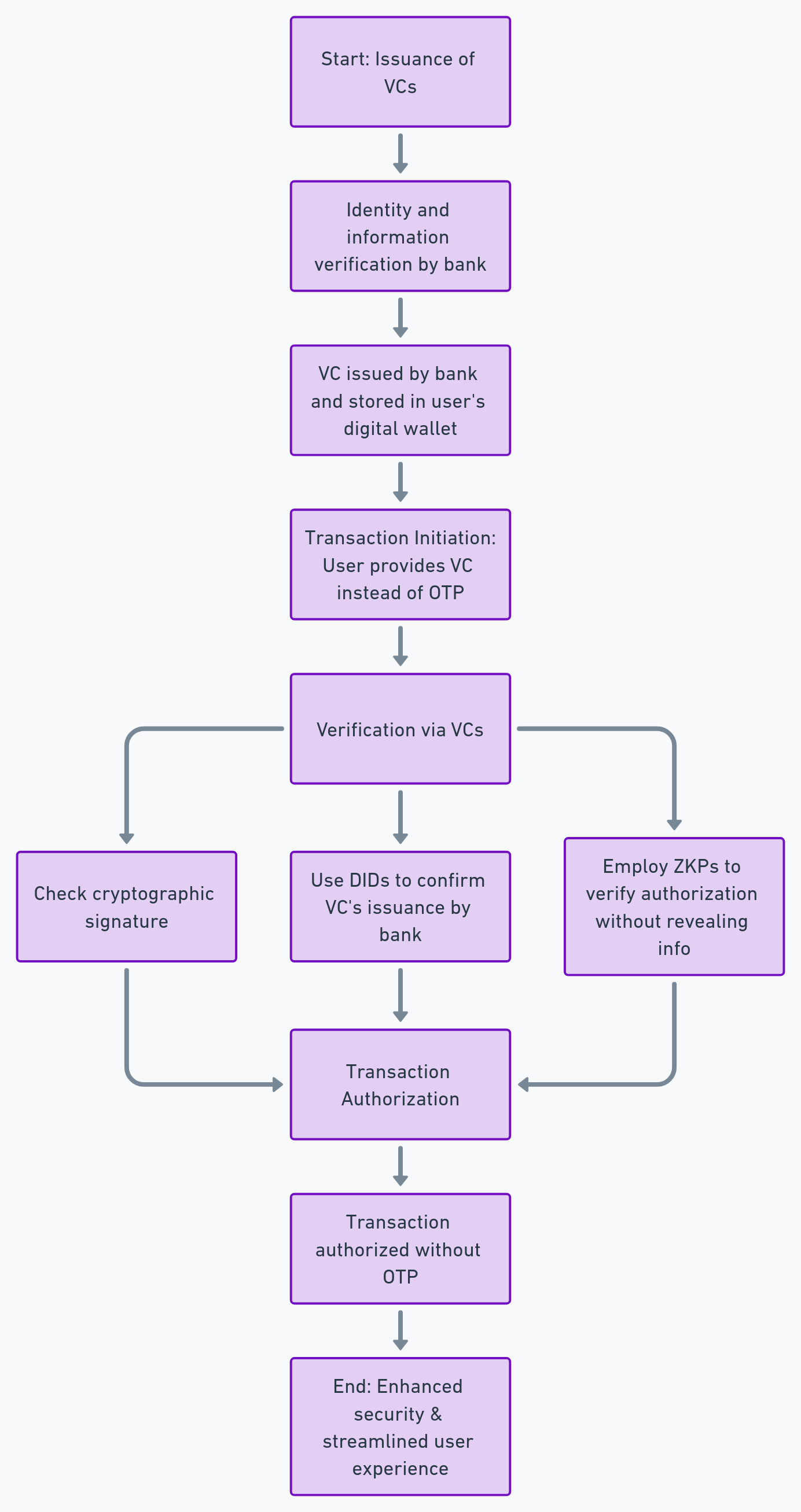
The integration of VCs into digital payment systems requires a reconfiguration of the authentication and authorization mechanisms currently dominated by OTPs. Here's how it could work technically:
Step 1: Issuance of VCs
Users would first need to obtain VCs from a trusted issuer, such as their bank or financial institution. This could involve verifying their identity and other relevant information through traditional means, after which the VC is issued and stored in the user's digital wallet.
Step 2: Transaction Initiation
When initiating a transaction, instead of receiving an OTP, the user would be prompted to provide a VC as proof of their identity and authorization to conduct the transaction.
Step 3: Verification via VCs
The payment gateway or transaction processor would then verify the VC by:
- Checking the cryptographic signature to ensure it's valid and hasn't been tampered with.
- Using DIDs to confirm the VC's issuance by a trusted authority.
- Employing ZKPs to verify the transaction's authorization without revealing unnecessary information.
Step 4: Transaction Authorization
Upon successful verification, the transaction is authorized without the need for an OTP. This process not only enhances security by leveraging cryptographic proofs but also streamlines the user experience by eliminating the need to manually enter OTPs.
Let’s look at this process with the help of a diagram:
The shift from OTPs to VCs for financial transactions represents a significant advancement in digital security and user experience. By leveraging cryptographic signatures, decentralized identifiers, and zero-knowledge proofs, VCs offer a more secure, efficient, and privacy-preserving alternative to traditional OTP systems. For platforms like Hypersign, which are at the forefront of implementing Self-Sovereign Identity solutions, this transition opens up new avenues for innovation and collaboration with financial institutions eager to adopt next-generation authentication methods.
About Hypersign
Hypersign is an innovative, permissionless protocol that manages digital identity and access rights. Rooted in the principles of Self-Sovereign Identity (SSI), Hypersign empowers individuals to take control of their data and access on the internet. It provides a scalable, interoperable, and secure verifiable data registry (VDR) that enables various use cases based on SSI. Built using the Cosmos-SDK, the Hypersign Identity Network is recognized by W3C (World Wide Web Consortium), promoting a seamless and secure Verifiable Credential and Decentralized Identifier management.
Get in touch with us today to understand the nuances of the decentralized identifier, Verifiable Credential, and on-chain KYC at meet.hypersign@gmail.com